Recent webinars have focused on a variety of proven, resilient technologies to combat GNSS and PNT vulnerabilities in critical infrastructure. In this webinar, we will focus on how PNT monitoring can further protect critical systems from these vulnerabilities through continuous monitoring and improvement. Similar to cybersecurity for network system...
In today's modern network infrastructure, millions of dollars are spent to ensure that networks are reliable, highly available, and most of all, secure! Cybersecurity has emerged as the critical area in all facets of the internet, yet still, there are often-overlooked areas which can degrade security measures meant to protect. One such example is t...
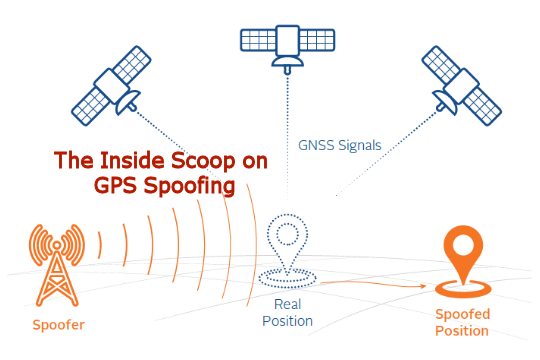
By Tyler Hohman, Director of Products, Orolia Defense & Security Most in our industry are aware of the threat that GPS interference poses, both in the US and overseas. GPS jamming is commonplace. Spoofing, however, is different than jamming in that it can be utilized in a far more devious manner. Both jamming and spoofing have a common goal – t...
Network cybersecurity is top of mind these days for both government agencies and commercial enterprise. As the heart of network synchronization, time and frequency systems should include a standard suite of security features that give network administrators confidence in the cybersecurity protocols of their time servers. This is our philosophy at O...
Network experts already know that distributing the correct time is key to maintaining their critical infrastructure programs. However, keeping accurate time is also fundamental to many cybersecurity applications. Certificates have an expiration date attached to them, and system logs frequently contain time stamps that operators rely on for diagnosi...